Over the last couple of years, online retail has gained global popularity, and together with it, a great need for proper security arose. Customers entrust online shops with their payment details and other sensitive personal information, which makes them extremely attractive to criminals and hackers. At the time like this, security must be the primary priority for online shop owners.
In this article, we will explore the best security measures for PrestaShop ecommerce platform. Also, we will learn about hacker attacks, that are most commonly used to breach the security of PrestaShop stores, and how to deal with them.
Table of contents:
Basic PrestaShop security measures from hackers
Install SSL certificate at the store
Utilize .htacess file to secure backend files
Delete the unnecessary files after installation
Deny access to your templates
Create backup copies of your store
Introduce cookies
Hacking techniques commonly applied to PrestaShop
Basic PrestaShop security measures from hackers
Update the PrestaShop version in time
Each new PrestaShop version has, among all other improvements, upgraded security and fixed vulnerabilities. Therefore, it is crucial that you utilize the latest stable version of the platform.
Install SSL certificate at the store
SSL certificate encrypts the data that is sent from the client to the web server and back. SSL certificates are considered one of the most basic and necessary security measures.
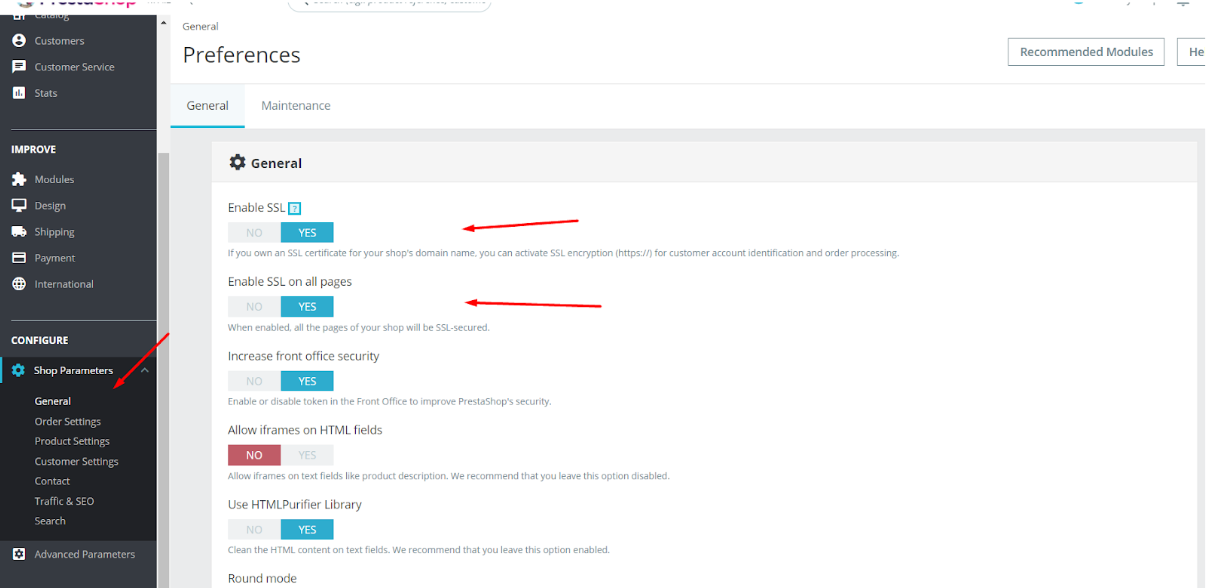
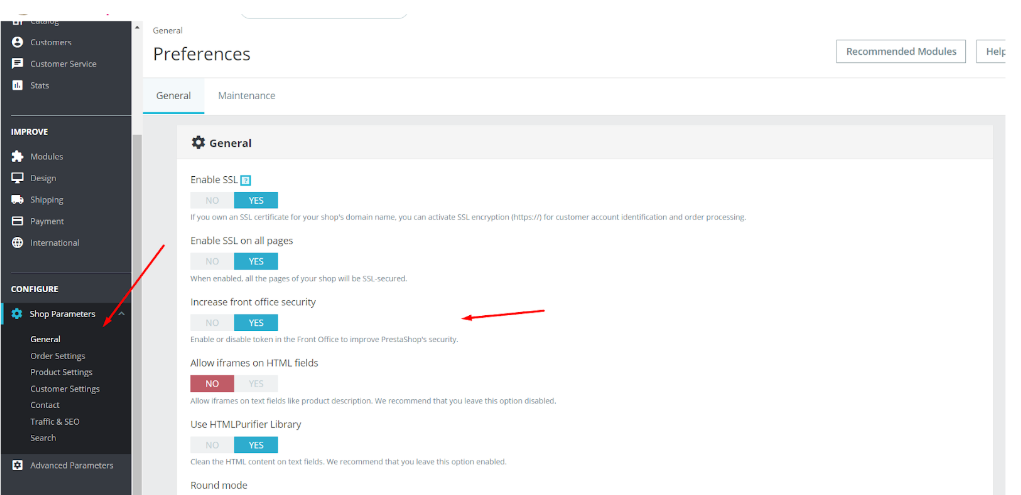
SSL can be enabled via PrestaShop admin panel. To do this, log in to the admin, navigate to Administration -> Shop Parameters -> GENERAL. Set Enable SSL and Enable SSL on all pages at Yes.
Utilize .htacess file to secure backend files
With the help of .htacess you can introduce additional safety measures, for instance, restrict access to the admin panel by creating a white list of IP addresses that will solely have access to it.
|
1 2 |
deny from all allo from X.X.X.X (IP address) |
Rename you backoffice folder
After you have installed PrestaShop, rename the admin folder for extra security. Ideally, the name should be unique and consist of both letters and numbers, for example, m8y1adm1n.
Delete the unnecessary files after installation
For security’s sake, it is strongly recommended to delete /install folder after you have upgraded or installed a new version of PrestaShop. Also, always delete the extra files from the server: README.md, CONTRIBUTING.md and CONTRIBUTORS.md files, as well as / docs file together with its contents.
Deny access to your templates
Block the access to the files and templates of your theme, using the .htaccess file with the following contents:
|
1 2 3 4 |
<FilesMatch "\.tpl$"> order deny,allow deny from all </FilesMatch> |
Create backup copies of your store
Having a backup copy of the webstore will allow you to fully restore it in case it will be hacked or break down. You can create a backup copy yourself or turn to a hosting company.
Introduce cookies
Cookies are the text files that contain information about the clients and visitors of your PrestaShop store.
You can turn cookies on and off via the admin panel. First, log in to your admin and navigate to Administration -> Shop Parameters -> GENERAL. Then, enable the Increase front office security to turn on cookie files for your store.
In addition to cookies, enabling Increase front end security will check the token data. When a customer will perform certain actions with the shopping cart, his token files will be sent to the server via GET or POST (in addition to COOKIE) to check if his IP and the browser cookies match. This will help to prevent frauds and unauthorized attempts to log into the admin panel.
Bear in mind that according to GDPR law a retailer must inform their customers the store uses cookies.
The main advantage of HTTPS protocol is that it makes the store much more safe for the visitors; in particular, the process of transferring customer data to the webstore. The aspect of such safety is particularly acute for the resources that require to fill in the credit card details or other sensitive personal information.
Data safety is ensured by SSL/TLS cryptographic protocols that have 3 levels of security:
- Data encryption, that prevents data interception.
- Data integrity, that documents every change in the information.
- Authentification, that keeps the user from the redirect.
Differences between HTTP and HTTPS:
- HTTPS is not a separate data transfer protocol, but a secure version of an HTTP protocol,
- data transferred via HTTP protocol is not secured, while HTTPS encrypts the information, thus securing it,
- HTTP uses port 80, HTTPS – port 443.
Hacking techniques commonly applied to PrestaShop
SQL Injection in Prestashop
SQL injection — is one of the common ways of hacking a website. It is carried out by placing into the data, transferred via GET and POST or Cookie, a malicious SQL code.
Here are the examples of the basic SQL injections:
- Collapsing the WHERE conditions to the true result despite the parameter values.
- Joining to a query the results of another query via UNION operator.
- Commenting on the part of a query.
The protection from SQL injections is not complicated and, in a nutshell, consists of keeping an eye on all sorts of data, converting numbers into numeric data type and enclosing the lines into backslashes (\) (this method is called screening). Also, PrestaShop ORM allows to make queries without screening.
Example:
We have a request for information via id
?id=1
Normally, this would mean getting an id in the form of a numeral.
SELECT id, name from table where id =1.
But since there is no typecasting, we can transfer via SQL injections the following type of data.
/?id=1+union+select+0,concat_ws(0x3a,table_name,column_name)+from+information_s chema.columns
In this case, SQL quiery will be the following:
SELECT id, name from table where id =1 union select 0,concat_ws(0x3a,table_name,column_name) from information_schema.columns
Moreover, a store owner must also be aware of Blind SQL Injection that is often implemented to aquire passwords.
/?id=1+AND+555=if(ord(mid((select+pass+from+users+limit+0,1),1,1))=97,555,777)
SELECT id, name from table where id =1 AND 555=if(ord(mid((select pass from users limit 0,1),1,1))=97,555,777)
In case the users table contains the pass column and the first symbol of the first entry equals 97 (symbol “a”), then DBMS will return TRUE; otherwise, it will be FALSE.
Another example of SQL injections is reading of the files:
|
1 |
union select load_file('/etc/passwd') |
Cross-site Scripting in PrestaShop
One of the most popular types of attacks is javascript cross-site scripting. This is a type of attack that injects malicious code into a web system, forcing it to issue changed data, replace links (visible / hidden) or display its own advertising on the affected resource.
With a combination of tags and symbols, a hacker creates such a request that the site understands and executes as a command. Once a security breach is found, they can attach malicious code to the request, which will, for example, steal cookies and send it to the hacker.
Using cross-site scripting, a person can:
- Introduce malicious code in the message.
- Upload scripts to steal administrator cookies from a malicious domain.
- After receiving the cookie, the attacker can log in as an administrator, which gives them a free hand for further attacks. Moreover, an attacker can connect an administrator browser and launch browser exploits.
Most of the vulnerabilities are associated with improper processing of data received from the outside, or insufficient data checking.
To secure your PrestaShop store from cross-site scripting, one can take the following actions:
1. The filter must take into account all possible character combinations. One of the simple xss vulnerability checks is the use of open and closed brackets.
For example:
|
1 |
“/?, #” >>>> << script {()} |
For security’s sake, implement the shielding the input / output data. To do this, you can use the built-in functions to clean the code from malicious scripts. These include such functions as htmlspecialchar (), htmlentities () and strip_tags (), addslashes ().
2. Set HttpOnly flag. This flag makes client cookies inaccessible through JavaScript. This setting is activated in php.ini:
|
1 |
session.cookie_httponly = True |
3. Use Content Security Policy.
This enables you to declare a list of sources from which you can load various data, for example, JS, CSS, images and other files. Even if the hacker manages to inject the script into a web page, it will not be executed if it does not correspond to the allowed list of sources.
4. Specify encoding on each page.
|
1 |
header ("Content-Type: text / html; charset = utf-8"); |
5. Setting permissions on folders and files.
6. Closing ports on the server. After installing and configuring the server some ports could be left open, and hackers can make use of them. Therefore, it is recommended to block or filter ports.
Wrapping it up
Unfortunately, there is no perfect solution and every new module, a plugin may contain problems. Therefore, always keep an eye on the data you add to the store. Even if the plugin or theme is approved and verified by the platform developers, it is better to check twice.
One thing is clear – a webstore should be protected against hackers and security accidents. Therefore, it is necessary to establish appropriate security measures and use additional resources to increase security.